基于数据挖掘的网络入侵检测的应用研究

1.无需注册登录,支付后按照提示操作即可获取该资料.
2.资料以网页介绍的为准,下载后不会有水印.资料仅供学习参考之用.
密 惠 保
基于数据挖掘的网络入侵检测的应用研究(论文12000字,外文翻译)
摘要:在今天飞速发展的计算机技术中,网络安全是需要我们重点解决的计算机网络问题之一。随着网络基础设施建设越来越完善和计算机用户飞速增长,网络与信息安全存在越来越多的问题,因黑客入侵其他计算机而造成的损失也越来也大。在我们的日常生活的整个世界里,信息、信息产品、信息资产等等信息相关极为重要。从具体发生的安全事件中我们可以发现重视网络安全的重要性。
本文将数据挖掘的相关知识和入侵检测技术结合起来,可以对网络安全进行良好的防护。本文具体介绍了数据挖掘和入侵检测的基本概念做了相关介绍。其中具体详细的介绍了数据挖掘的几种算法。包括这几种算法的具体原理,在进行入侵检测时它们存在的优缺点,并提出了算法改进的方法。
最后本文使用KDDCup99数据库的数据进行测试。网络连接有41个属性特征,数据有四类基本特征。实验获得了只用聚类算法进行实验的结果、两种数据挖掘算法结合所的实验结果,并将这两种实验结果进行了对比分析。最后对实验总结与展望。
关键词:数据挖掘;入侵检测;测试;聚类算法
Application research of network intrusion detection based on data mining [资料来源:http://think58.com]
Abstract:In today's rapid development of computer technology, network security is one of the computer network problems we need to focus on. With the development of network infrastructure and the rapid growth of computer users, there are more and more problems in network and information security. In the whole world of our daily life, information, information products, information assets and so on information correlation is extremely important. From the specific security incidents we can find that the importance of network security.
This paper combines the relevant knowledge of data mining with intrusion detection technology to protect network security. This paper introduces the basic concepts of data mining and intrusion detection. Some algorithms of data mining are introduced in detail. Including the specific principles of these algorithms, the advantages and disadvantages of them in intrusion detection, and proposed the algorithm improvement method.
Finally, the data from KDDCup99 database is used for testing. Network connection has 41 attributes and data has four basic characteristics. The experimental results are obtained by using only clustering algorithm and combining the three data mining algorithms. The three experimental results are compared and analyzed. Finally, the conclusion and prospect of the experiment are given. [资料来源:www.THINK58.com]
Key words: data mining; intrusion detection; test ;clustering algorithm
[来源:http://www.think58.com]
目录
1、绪论 1
1.1论文研究意义 1
1.2入侵检测技术的发展 1
2、入侵检测与数据挖掘 1
2.1网络入侵检测的环境分析 1
2.2入侵检测分类 2
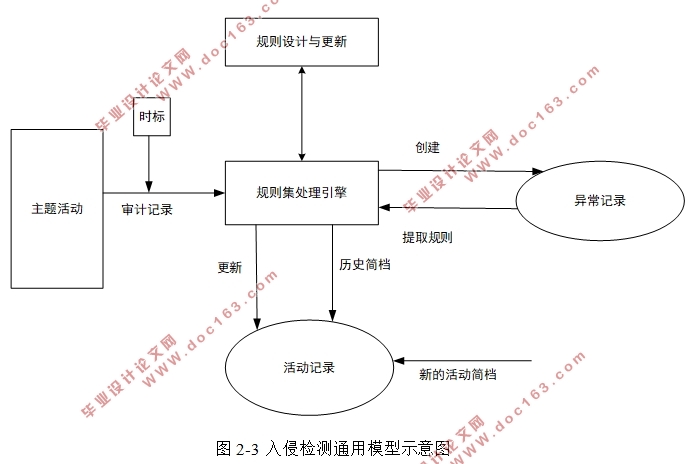
2.3入侵检测相关介绍 3
2.4数据挖掘概述 4
2.5数据挖掘与入侵检测结合分析 5
2.6总结 6
3、基于数据挖掘的网络入侵检测算法 6
3.1聚类算法 6
3.2关联规则算法分析 8
3.3混合算法 13
3.4总结 14
4、实验与结果分析 14
4.1实验数据采集 14
4.2数据预处理 16
[资料来源:THINK58.com]
4.3实验结果分析 18
4.4两种实验结果对比分析 20
4.5总结 21
5、总结与展望 21
参考文献...................................................................................... ......21
[来源:http://www.think58.com]
