基于混沌的数字图像加密及性能研究
1.无需注册登录,支付后按照提示操作即可获取该资料.
2.资料以网页介绍的为准,下载后不会有水印.资料仅供学习参考之用.
密 惠 保
基于混沌的数字图像加密及性能研究(论文22000字)
摘要:
本文主要分为三个部分:
第一部分主要研究相关理论,包括混沌理论、密码学理论、图像加密置乱算法和扩散算法、混沌数字图像密码系统的性能评价方法。用Matlab对图像进行了行置乱和列置乱变换,实现了典型的图像加密。
第二部分首先介绍了典型的混沌图像加密系统,考虑到典型图像密码系统的密码仅与密钥有关,与明文无关,易受选择明文攻击或已知明文攻击。在参考了传统的既与密钥有关又与明文图像有关的明文关联加密算法的基础上,本文使用了明文无关的扩散算法以及明文关联的置乱算法,在混沌密码发生器中用分段线性混沌映射(PWLCM)代替传统的超混沌Lorenz系统映射,构建了一个新的基于分段线性映射的明文关联混沌图像密码系统,并用Matlab仿真实现了该算法对图像的加密及解密。
第三部分使用Matlab软件,首先对该算法加密与解密速度、密钥空间和信息熵进行测试,其次从直方图、2检验结果和相关系数对密文统计特性进行测试,接着通过高斯、椒盐和裁剪攻击,并分析计算了NPCR、UACI和BACI数值,对该算法的密钥敏感性、明文敏感性和密文敏感性进行测试。结果表明,该算法的加密与解密速度快,密钥空间大,信息熵接近理想状态,密文统计特性良好,密钥敏感性、明文敏感性及密文敏感性均较强,该明文关联加密算法性能良好,能够抵抗各种攻击。 [资料来源:THINK58.com]
关键字:混沌;数字图像加密;明文关联;安全性能
Chaotic digital image encryption and its performance analysis
Abstract:
With the rapid development of Internet technology, multimedia applications are becoming more and more widespread. Digital images play an important role in the field of multimedia information. Digital images can convey intuitively rich information. The Internet is an open platform. Transmitting digital images on the Internet is vulnerable to security problems such as tampering and theft. In the increasingly prominent situation of Internet security threats, the most direct and effective method for securing digital images in network transmission is to encrypt digital images.
This article is mainly divided into three parts:
The first part mainly studies related theories, including chaos theory, cryptography theory, image encryption scrambling algorithm and diffusion algorithm, performance evaluation method of chaotic digital image cryptography system. Using Matlab, the image was scrambled and column scrambled to achieve a typical image encryption. [资料来源:http://www.THINK58.com]
The second part first introduces a typical chaotic image encryption system. Considering that the password of a typical image cryptosystem is only related to the key, it has nothing to do with plaintext and is vulnerable to the choice of plaintext attack or known plaintext attack. After referring to the traditional plaintext association encryption algorithm that is related to both the key and the plaintext image, this paper uses the plaintext-independent diffusion algorithm and the plaintext associated scrambling algorithm, and uses piecewise linear in the chaotic cipher generator. The chaotic map (PWLCM) replaces the traditional hyperchaotic Lorenz system mapping, and a new piecewise linear mapping-based plaintext relational chaotic image cryptosystem is constructed. The algorithm is used to encrypt and decrypt images using Matlab simulation.
The third part uses Matlab software to test the algorithm's encryption and decryption speed, key space, and information entropy first, and then tests the statistical characteristics of the ciphertext from the histogram, c2 test results, and correlation coefficients, and then passes Gaussian, salt and pepper, and The attack was cropped, and the NPCR, UACI and BACI values were analyzed and calculated. The key sensitivity, the plaintext sensitivity and the ciphertext sensitivity of the algorithm were tested. The results show that the algorithm has fast encryption and decryption speed, large key space, close to ideal information entropy, good ciphertext statistics, strong key sensitivity, plaintext sensitivity, and ciphertext sensitivity. The algorithm has good performance and can resist various attacks.
Key words: Chaos; Digital Image Encryption; Plaintext Correlation; Security Performance
[资料来源:THINK58.com]

目 录
1 绪论 1
1.1课题研究背景与意义 1
1.2国内外研究状况 1
1.3本文研究的主要内容 2
2 混沌密码与混沌图像加密技术基础 2
2.1混沌理论 2
2.1.1混沌定义 2
2.1.2混沌系统的相关特性 3
2.2混沌密码理论 4
2.2.1混沌密码基本概念 4
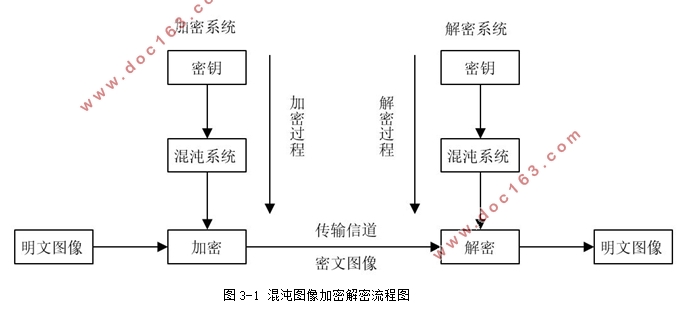
2.2.2加密系统结构 4
2.2.3密码分析攻击分类 5 [资料来源:THINK58.com]
2.2.4混沌理论与密码学之间的关系 5
2.3图像加密相关知识 6
2.3.1图像加密概念 6
2.3.2基于混沌的图像加密技术 6
2.4图像加密置乱算法和扩散算法基本理论 7
2.4.1图像加密置乱算法 7
2.4.2图像加密扩散算法 8
2.5混沌加密性能评价指标 9
2.5.1图像加密/解密速度 9
2.5.2密匙空间 10
2.5.3密文统计特性 10
2.5.4图像分析 10
2.5.5信息熵 11
2.6图像密码系统的敏感性分析方法 11
2.6.1密钥敏感性分析 12
2.6.2明文敏感性分析 12
2.6.3密文敏感性分析 12
3 明文关联混沌图像密码系统构建及其Matlab仿真 13
3.1典型混沌图像加密系统 13
3.2一种基于分段线性映射的明文关联混沌图像密码系统 14
[资料来源:http://www.THINK58.com]
3.3该系统的图像加密与解密方案 14
3.3.1混沌密码发生器 15
3.3.2明文无关的前向扩散模块 15
3.3.3明文关联的置乱模块 15
3.3.4明文无关的后向扩散模块 16
3.4Matlab仿真过程与结果 16
4 明文关联的混沌图像密码系统性能测试 18
4.1加密与解密速度测试 18
4.2密钥空间测试 18
4.3信息熵测试 19
4.4密文统计特性测试 19
4.5密钥敏感性测试 22
4.6明文敏感性测试 24
4.7密文敏感性测试 26
4.8明文关联置乱图像密码系统性能评价 28
5 总结与展望 28
5.1总结 28
5.2展望 28
参考文献 29
致谢 30
附录 31
