基于深度学习的网络行为取证研究(Python)

1.无需注册登录,支付后按照提示操作即可获取该资料.
2.资料以网页介绍的为准,下载后不会有水印.资料仅供学习参考之用.
密 惠 保
基于深度学习的网络行为取证研究(Python)(论文11000字,参考代码,部分实验图)
摘要:随着信息科技的飞速发展,网络安全问题日益明显。传统网络攻击应对方案难以应付如今复杂的网络环境。因此,基于深度学习技术的相关知识,本文构造了两种基于深度学习的网络攻击行为的取证检测模型,目的是对常见的几种网络攻击行为进行准确识别。本实验对深度神经网络(DNN)与卷积神经网络(CNN)两种模型进行了全面介绍,在将KDD99数据集中网络数据转换为数字表示的函数后,使用ReLU激活函数来缓解神经网络构建时可能发生的梯度消失和过拟合问题,以均方误差(MSE)为误差函数,使用随机梯度下降法(SGD)调参,对比两种神经网络模型的准确性与时间效率。实验结果表明,文本基于DNN与CNN的网络攻击取证模型在识别的准确率上达到0.9910(DNN)与0.9904(CNN)。两者训练时间相差无几,DNN模型的准确率更高。
关键词:深度学习,深度神经网络,卷积神经网络,网络攻击取证
Research on Network Behavior Forensics Based on Deep Learning
Abstract:Network security issues are becoming more and more obvious. Traditional cyberattack solutions are difficult to cope with today's complex network environments. Therefore, based on the relevant knowledge of deep learning technology, this paper constructs two forensic detection models based on deep learning network attack behavior, the purpose is to accurately identify several common network attack behaviors. In this experiment, the deep neural network (DNN) and convolutional neural network (CNN) models are introduced. After the KDD99 dataset network data is converted into a digital representation function, the ReLU activation function is used to alleviate the neural network construction. The gradient disappearance and over-fitting problems may occur. The mean square error (MSE) is used as the error function, and the stochastic gradient descent method (SGD) is used to adjust the parameters to compare the accuracy and time efficiency of the two neural network models. The experimental results show that the text based on DNN and CNN network attack forensics model has an accuracy of 0.9910 (DNN) and 0.9904 (CNN). The training time of the two is almost the same, and the accuracy of the DNN model is higher.
[版权所有:http://think58.com]
Key words: Deep learning, convolutional neural networks, network attack behavior
目录
1 绪论 5
1.1研究背景和意义 5
1.2国内外研究现状 5
1.3主要研究内容 6
2网络行为检测相关知识体系 6
2.1行为检测 6
2.2深度学习 6
2.3神经网络 6
2.4损失函数 8
2.5参数更新 9
2.6相似性度量 10
3网络攻击检测与基本模型 11
3.1网络攻击分类 11 [来源:http://think58.com]
3.2检测系统与技术分类 11
3.3深度神经网络 12
3.4卷积神经网络 12
4网络攻击行为研究 13
4.1基本框架 13
4.2数据处理 13
4.3神经网络的搭建与训练 15
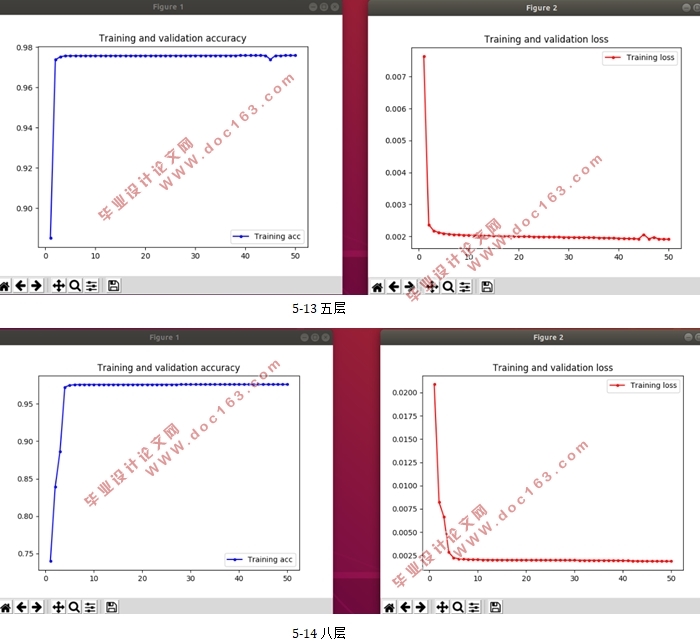
5实验与分析 16
5.1 实验环境 16
5.2数据集分析 17
5.3基于DNN的网络攻击检测 17
5.4基于CNN的网络攻击检测 19
5.5实验对比与总结 21
6 总结与展望 23
参考文献: 24
致谢 26
